Log formats of Wcol-E and its example
Goto examples
Overivew
Wcol-E, the prefetching proxy server writes logfile. Using logfile analysis, you will know number of access, traffic and fashion of users. This page shows its format and examples.
Overview
Log types
Select log-type which you want. Type is located in 7th field in specified logfile or system logfile.Tips
deamons log
START
1 time(sec.usec)
2 START
3 version of Wcol-E
4 ID of information format
5 mode, PROXY/CATALYST
END
1 time(sec.usec)
2 END
3 version of Wcol-E
4 ID of information format
sessions log
Generic pattern:
1 time(sec.usec)
2 session, FETCH/SEND/PREFETCH
3 service port
4 peer-address (client or child proxy)
5 request protocol, HTTP/ICP
6 request protocol version
7 no-cache ('n' if no-cache)
8 if-modified-since[IMS] ('*' if specified time)
9 auth ('X' if authorized)
10 method, GET/HEAD/POST
11 URL
12 HTTP response-code
13 content-type
14 size to client (bytes)
15 response time to client (msec)
16 :
HTTP
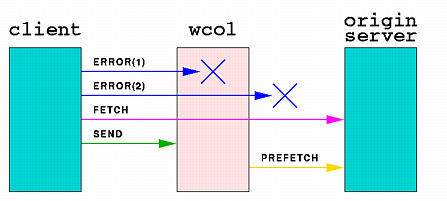
1 time(sec.usec)
2 session, FETCH
3 service port
4 peer-address (client or child proxy)
5 request protocol, HTTP
6 request protocol version
7 no-cache ('n' if no-cache)
8 if-modified-since[IMS] ('*' if specified time)
9 auth ('X' if authorized)
10 method, GET/HEAD/POST
11 URL
12 HTTP response-code
13 content-type
14 size to client (bytes)
15 response time to client (msec)
16 :
17 server-type, ORIGIN/PARENT/SIBLING
18 server
19 server-port
20 size from server (bytes)
21 response time from server (msec)
PREFECH
1 time(sec.usec)
2 session, PREFETCH
3 service port
4 peer-address (client or child proxy)
5 request protocol, HTTP
6 request protocol version
7 no-cache ('n' if no-cache)
8 if-modified-since[IMS] ('*' if specified time)
9 auth ('X' if authorized)
10 method, GET/HEAD/POST
11 URL
12 HTTP response-code
13 content-type
14 size to client (bytes)
15 response time to client (msec)
16 :
17 server-type, ORIGIN/PARENT/SIBLING
18 server
19 server-port
20 size from server (bytes)
21 response time from server (msec)
SEND
1 time(sec.usec)
2 session, SEND
3 service port
4 peer-address (client or child proxy)
5 request protocol, HTTP
6 request protocol version
7 no-cache ('n' if no-cache)
8 if-modified-since[IMS] ('*' if specified time)
9 auth ('X' if authorized)
10 method, GET/HEAD/POST
11 URL
12 HTTP response-code
13 content-type
14 size to client (bytes)
15 response time to client (msec)
16 :
17 date-source, CACHE
18 -
19 -1
20 size from server (bytes)
21 response time from server (msec)
22 :
23 reason, FETCH/PREFETCH
24 apperence count
ERROR
1 time(sec.usec)
2 session, ERROR
3 service port
4 peer-address (client or child proxy)
5 request protocol, HTTP
6 request protocol version
7 no-cache ('n' if no-cache)
8 if-modified-since[IMS] ('*' if specified time)
9 auth ('X' if authorized)
10 method, GET/HEAD/POST
11 URL
12 HTTP response-code
13 content-type
14 size to client (bytes)
15 response time to client (msec)
16 :
ICP
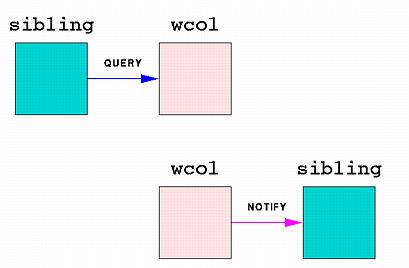
1 time(sec.usec)
2 session, QUERY
3 service port
4 peer-address (client or sibling proxy)
5 request protocol, ICP
6 request protocol version
7 no-cache ('n' if no-cache)
8 if-modified-since[IMS] ('*' if specified time)
9 auth ('X' if authorized)
10 method, QUERY
11 URL
12 response, HIT/MISS
13 -
14 size to client (bytes)
15 -
16 :
GC (Garbage Collector)
GC START
1 GC
2 START
3 time (sec)
4 buffer legth for GC
5 path of GC working file
GC END
1 GC
2 END
3 time (sec)
4 take time for GC
5 cache size after GC
6 cache size before GC
7 cache size before GC (directories)
8 cache size before GC (files)
9 cache legth before GC (number of files)
10 size of expired unused cache