
Improving future society trustworthiness through security research
Cybersecurity Laboratory
Associate Professor:BEURAN Razvan
E-mail:
[Research areas]
Cybersecurity, IoT/CPS security
[Keywords]
Network security, AI, Trustworthiness, Security training, Cyber range
Skills and background we are looking for in prospective students
We welcome students with interests and abilities related to cybersecurity and network security, as well as good programming skills.
Independent thinking and a strong motivation to learn and develop oneself are a must.
What you can expect to learn in this laboratory
Students who graduate from our lab will possess deep knowledge regarding cybersecurity and IoT/CPS security. They will be able to develop cybersecurity-related software, and perform various kinds of network experiments and assessments. The students will also gain hands-on network security experience and will be capable to deal with cybersecurity issues in the real world. Their English paper reading and writing, as well as presentation skills will also improve significantly.
【Job category of graduates】 Cybersecurity, ICT, embedded system manufacturing
Research outline
Overview
According to the vision put forward by the Japanese government regarding the future digital society, also known as Society 5.0, the cyber and physical spaces will be tightly integrated to build a human-centered society. Given that the Internet of Things (IoT) and Cyber Physical Systems (CPS) have already started to become an integral part of our daily life, new challenges and issues regarding their use arise.
These complex conditions place strong requirements regarding the trustworthiness of Society 5.0, and to address these issues our lab focuses on the following key research question: How to ensure that the future Society 5.0 is a safe and secure environment?
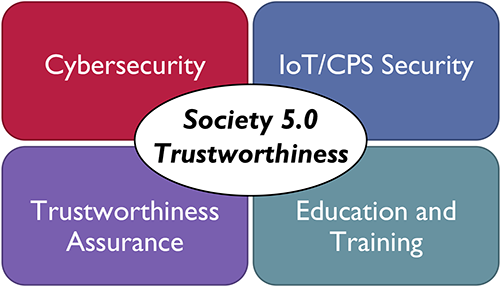
Research directions for ensuring the trustworthiness of Society 5.0
To answer this research question, our laboratory pursues four main research directions, as described next.
Cybersecurity
The increase of cybersecurity threats in our society makes it necessary to create robust systems that support a wide range of cybersecurity-related activities. For this purpose, we leverage many modern techniques, such as artificial intelligence and machine learning. Examples related to this research direction include: (i) Reinforcement learning agent training methodologies (e.g., for automated cyber defense); (ii) Cybersecurity-related information processing techniques (e.g., for attack path extraction from cyber threat intelligence reports).
IoT/CPS Security
IoT/CPS systems have specific characteristics, such as computation resource constraints and a complex System of Systems (SoS) nature. In order to address these issues, IoT/CPS security approaches require the use of suitable techniques, as highlighted in the following examples: (i) IoT network intrusion detection based on federated learning techniques; (ii) Smart building control system emulation platform for security testing.
Trustworthiness Assurance
Society 5.0 challenges must be thoroughly considered from the perspective of the five components of trustworthiness: safety, security, privacy, reliability and resilience. Related activities include: (i) Develop a trustworthiness assurance framework to provide guarantees for all the five trustworthiness components; (ii) Conduct a case study on smart building control systems.
Security Education and Training
The human factor is an important component of modern cybersecurity, and we conduct research in the areas of technical security training and security awareness training. Examples for this research direction are: (i) Development of the integrated cybersecurity training framework CyTrONE and the corresponding training content; (ii) Conducting hands-on training activities.
Key publications
- H. P. T. Nguyen, K. Hasegawa, K. Fukushima, R Beuran, “PenGym: Realistic training environment for reinforcement learning pentesting agents,” Elsevier Computers & Security, vol. 148, January 2025, 104140.
- K. Mai, J. Lee, R Beuran, R. Hotchi, S. E. Ooi, T. Kuroda, Y. Tan, “RAF-AG: Report analysis framework for attack path generation,” Elsevier Computers & Security, vol. 148, January 2025, 104125.
- R. Beuran, J. Wang, M. Zhao, Y. Tan, “IoT Security Training for System Developers: Methodology and Tools,” Elsevier Internet of Things, vol. 24, December 2023, 100931.
Equipment
HPC System “KAGAYAKI”
https://www.jaist.ac.jp/iscenter/mpc/kagayaki/
Teaching policy
We provide a dynamic research environment in which students can broaden their knowledge, learn new skills, and develop new abilities. We lay a strong emphasis on putting theoretical knowledge into practice through applied research, and on hands-on experience with various aspects of cybersecurity and network security. Since the development of communication skills is also extremely important, students are highly encouraged and supported to present and publish their research work.
[Website] URL : https://www.jaist.ac.jp/is/labs/beuran-lab/